
Key Takeaways
- Hospitality cyber security matters because it safeguards guests’ sensitive personal and financial information, helps you mitigate legal risks, and protects critical systems.
- Common travel industry data breaches include POS attacks, malware and ransomware infections, phishing attacks, Wi-Fi network hacks, DDoS attacks, and DarkHotel hacking.
- When implementing hotel cybersecurity best practices, you should consider scalability, ease of integration, access control and authentication, cloud security, and data privacy compliance.
Cybercrime has become a severe problem for hospitality and hotels in particular. Insider incidents aren’t as common as you think. According to the Data Breach Investigations Report, 90% of hospitality data breaches come from external actors. At the same time, 91% of cyber fraudsters are financially motivated, and 9% are engaged in espionage.
Each successful assault by hackers has its price. According to the 2022 report by the Ponemon Institute and IBM Security, a data breach in hospitality costs around $2.94 million. That’s why investments in cybersecurity in hospitality industry are money well spent.
“Large hotel chains often create their own mobile apps, booking systems, and so on. However, they do not always pay attention to the security of such software. For instance, guests’ credit card details and other personal data may be stored in unprotected databases on the hotel’s servers. As a result, this information becomes easy prey for hackers”, says Oleksii Glib, Founder at Acropolium.
This article deals with the question of why hospitality is especially vulnerable to data breaches. You will learn about the main data security threats in hotels and hospitality businesses and how to avoid them.
Why Does Hotel Cybersecurity Matter?
The hospitality industry is the focus of cybercriminals’ attention for several different reasons.
Financial
Hospitality businesses cause lots of security risks:
- Motivated by the desire to provide personalized experiences by using AI and ML, chatbots, and other technology tools, hospitality businesses accumulate more and more information. For example, credit card information, passport details, travel itineraries, personal preferences, etc.
- Loyalty point balances are under such scrutiny as credit card statements. Aside from stealing accumulated points, the latter may also get more personal information (full names, birthdates) and, as a result, crack more passwords and credentials.
- Some guests may be executives and other wealthy individuals, which are prime targets for hackers. Tapping into that stream of sensitive data may provide ample opportunities for fraudulent purchases and phishing attacks.
Physical
Hackers can breach one regional hotel and access the entire chain’s network. Each hotel provides many potential entry points for criminals: alarms, electronic door locks, Wi-Fi, climate control systems, numerous Internet of Things (IoT) devices, etc.
Human
High turnover poses challenges to managing permissions for different staff members. At the same time, one mistake by an unsuspecting employee can jeopardize the whole international chain.
Reputational
The consequences of cybersecurity failure may be catastrophic. The most obvious is a blow to brand reputation. Customers aren’t likely to trust the company, which didn’t manage to keep the personal data of their guests safe. Moreover, there are legal and financial penalties.
Most Well-Known Hotel Cybersecurity Incidents
- One of the most prominent hotel data breaches at Starwood hotels, which began in 2014, exposed 339 million guest records. In 2020, the UK Information Commissioner’s Office (ICO) fined Marriott International, the owner of Starwood, $24 million.
- InterContinental Hotel Group (IHG) was attacked in 2022. The incident started from a compromise of Starwood’s data and subsequently extended to the IHG group, encompassing over 6,000 hotels across 100 countries.
- Between 2008 and 2010, cybercriminals compromised about 619,000 of Wyndham’s customer records. The data breach resulted in clients losing more than $1.6 million to fraud. The hotel spent more than $5 million on legal fees and vendors to fix the data leak.
“The costs and reputation damage associated with security lapses are more costly to a hospitality brand than proactively investing in security solutions and programs before an incident,” says Jeff Venza, Chairman and CEO at Venza.
Common Security Threats in the Hospitality Industry
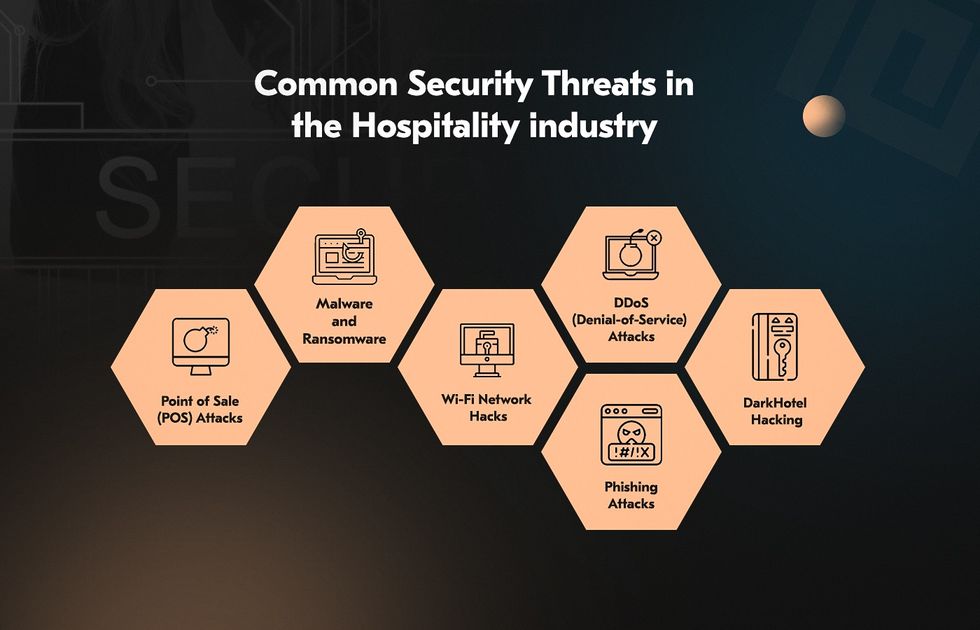
System intrusion, social engineering, and basic web application attacks represent 90% of hospitality breaches. Let’s take a look at them and possible ways to enhance cyber security in hospitality industry.
Point of Sale (POS) Attacks
These attacks, aiming for direct access to customers’ credit cards, are the most common ones in the sector. Hotels may have POSs (terminals at restaurants, parking lots, etc.) offering many entry points for hackers. Insecure remote access or a weak password at any of them is a way in for a cybercriminal.
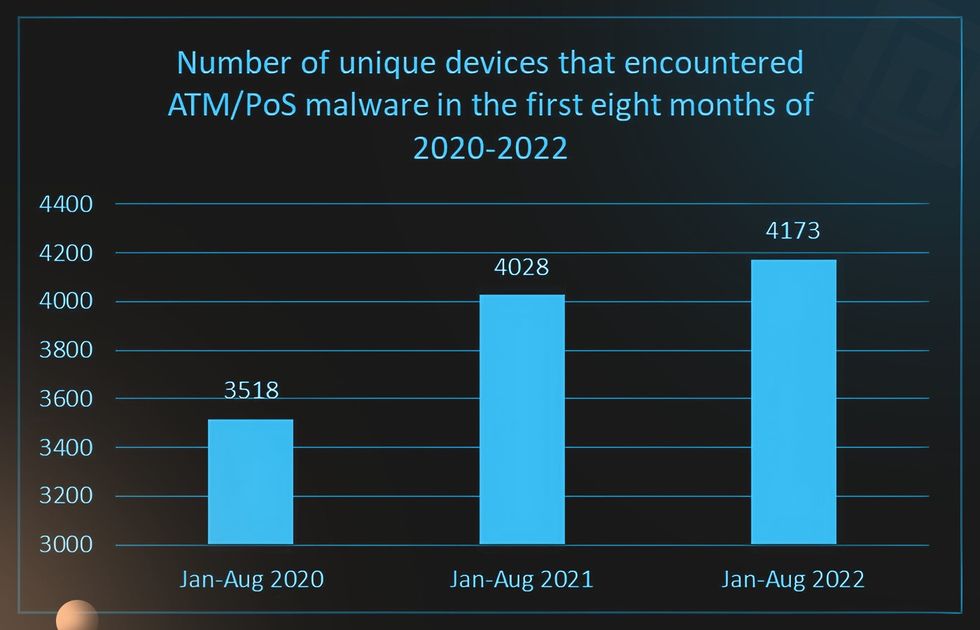
Since the beginning of the pandemic, the number of attacks has decreased dramatically. But once restrictions eased and old spending patterns returned, hacker activity picked up. In total, 4,173 devices were attacked between January and August 2022.
To protect against this threat, the company should:
- Comply with PCI standards across all networks, routers, and servers.
- Use end-to-end encryption, antivirus, and two-factor authentication on POS systems. By encrypting the cardholder’s data, a hotel can prevent hackers from easily accessing it in the event of a network breach.
- Hire a reputable data security provider.
- Monitor possible thefts of POS devices, regularly accounting for all of them.
Malware and Ransomware
Malware, or “malicious software,” infiltrates networks or individual computers, deleting files, stealing information, or installing unwanted software. Viruses, spyware, and so-called “trojan horses” fall into that category.
The computer or network can be infected when users install software, visit an infected website, click email attachments, pop-up windows, or links.
To protect against malware or ransomware, the hospitality company should:
- Keep browsers and anti-malware software up-to-date.
- Back up your big data regularly.
- Educate staff about avoiding security breaches in the hotel industry:
- Check flash drives for viruses before using them
- Be careful when clicking on links and advertisements
- Don’t give software from unknown or unreliable sources administrative permissions
Phishing Attacks
Phishing emails are designed to look like ones from a trustworthy sender. In those emails, the hackers try to lure recipients into sharing sensitive information, such as passwords or credit card details.
For instance, an attack may include a combination of a spear-phishing phone call and an email. The criminal calls the hotel to act as a dissatisfied ransomware customer. The “customer” offers to share more details about the case via email. An employee opens a follow-up email and will likely activate a malicious file. Thus, the hacker gets entry into the hotel network.
To protect against phishing attacks, try the following steps:
- Install and update software to detect phishing emails
- Train employees to spot phishing emails (suspicious email addresses, poor grammar, spelling, typos, etc.)
Wi-Fi Network Hacks
A fast Wi-Fi network is a must-have for a modern hotel. Hackers may try to install a rogue access point (AP), a wireless AP in a secure network, without an administrator’s authorization. As a result, criminals can hack the network from inside the hotel or even from a nearby car.
Another threat to cyber security in the hospitality industry is an evil twin AP, a fraudulent copy of a legitimate Wi-Fi AP. Hackers get close to the hotel and try to obtain AP information (MAC Address, SSID name, and Channel number). With this information, they can create a similar-looking AP. The hotel’s employees and guests inadvertently connect to the wrong AP.
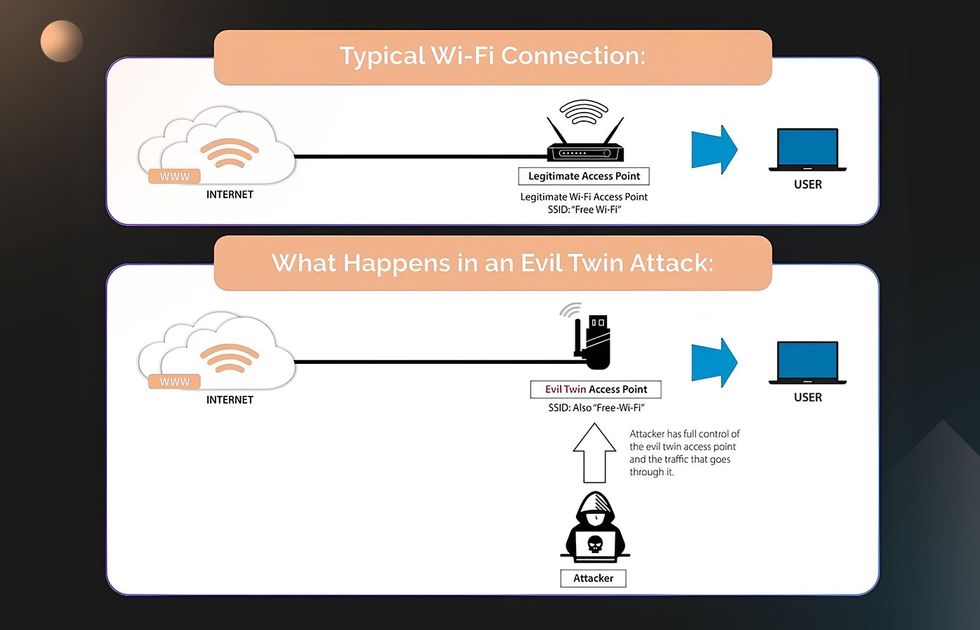
As a result, criminals can hack into guests’ laptops or smartphones. They can hijack personal data and passwords and infect the devices with malware. Besides, if a hotel’s database with information about guests isn’t adequately secured, hackers can also retrieve it.
You can protect guests and employees from Wi-Fi network attacks by:
- Using wireless intrusion prevention systems (WIPS), which can look for unauthorized access points by monitoring the radio spectrum
- Encouraging guests to use virtual private networks (VPNs), which provide an additional security layer
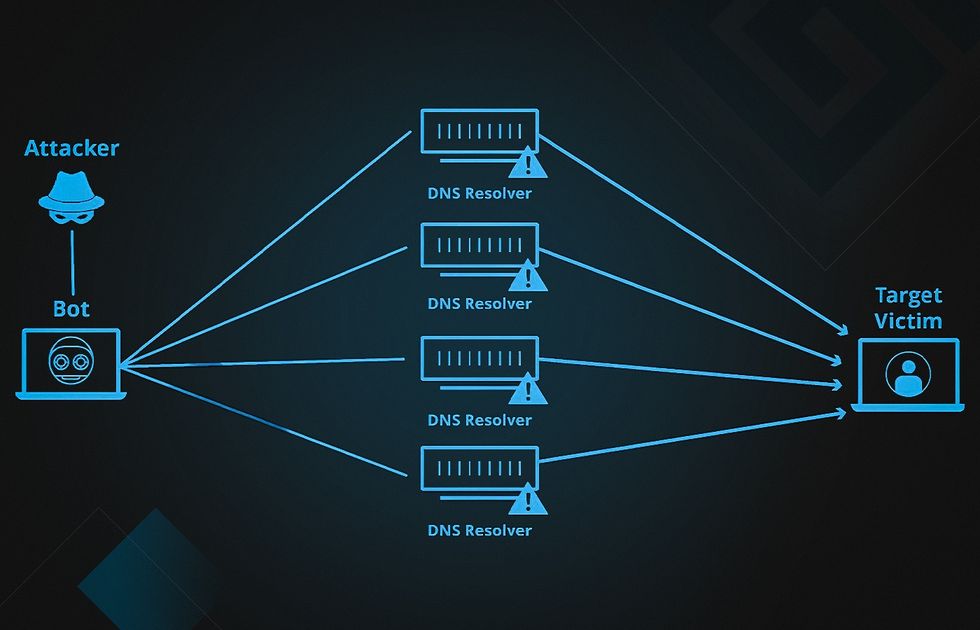
DDoS (Denial-of-Service) Attacks
A DDoS attack is an attempt to disrupt the functioning of a server or network by overloading it with internet traffic. Hackers use botnets of compromised networks to generate a powerful torrent of traffic. According to Kaspersky, a cybersecurity and anti-virus provider, the number of DDoS attacks in Q1 2022 rose 4.5 times compared to Q1 2021.
Hotels rely on many devices managed by computers: heating, ventilation, air conditioning systems, sprinklers, closed-circuit television systems, and more. Those devices can send pulses to infrastructure elements, bringing the whole system down. DDoS attacks can disable a hotel’s online billing systems, ticket booking, or official website.
To protect yourself against DDoS attacks:
- Employ anti-DDoS services to detect and deal with suspicious spikes in network traffic.
- Make sure firewalls and routers have the latest security patches and can reject “malicious” traffic.
DarkHotel Hacking
DarkHotel is a relatively new form of spear phishing. Hackers get the travel plans of their targets (usually C-level business executives and other VIPs). They can access a hotel’s Wi-Fi to upload malicious code on a server. Victims receive an invitation to download it as some benign update or program. If they do, the hacker gets access to information on their device.
Protection against DarkHotel hacking includes:
- Encouraging guests, especially VIPs, to protect their Internet traffic with a virtual private network (VPN)
- Warning guests about the dangers of clicking on pop-up messages if they use local public Wi-Fi. They will be better off downloading software from the partner’s website.
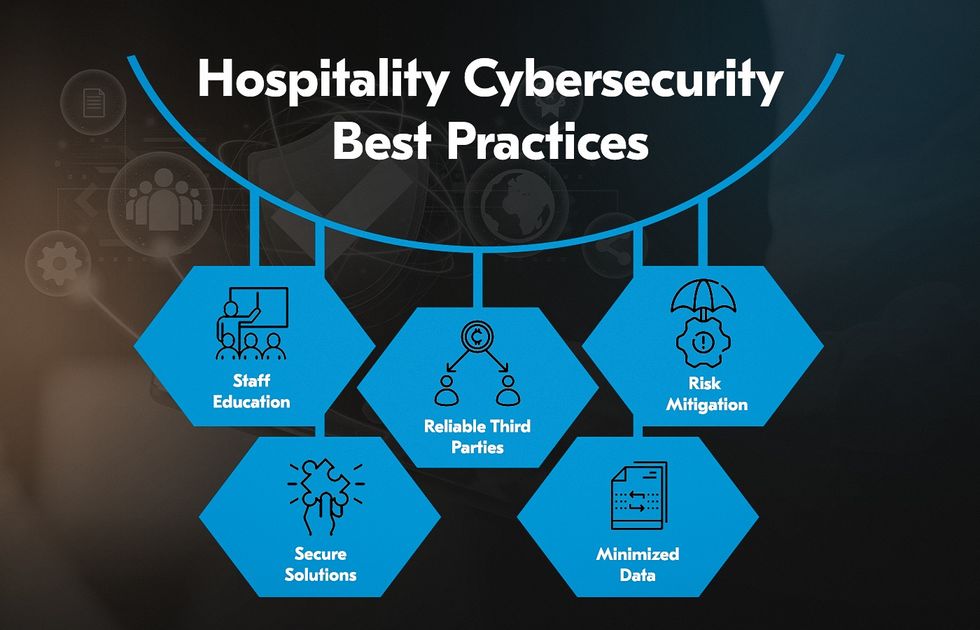
Hospitality Cybersecurity Best Practices
Hotel data breach threats are numerous and can be costly. You should devise the right strategy for cyber security for hotels, considering the following essential principles.
Staff Education
Educate your staff about cybersecurity threats. Tell employees about common hacker tactics, explain what they should do or avoid doing to protect themselves, their employer, and their guests. Teach them to be vigilant.
“Cybersecurity in the hospitality industry is everyone’s responsibility, whether you are C-level, management, accounting, housekeeping, maintenance, or reception, it does not matter. Everyone needs to be made aware of the hotel’s individual cybersecurity policies, attitude, and culture,” says Rob van der Heijden, Global Chief Security Officer at protel.
Reliable Third Parties
Hotel chains tend to create custom systems, managing credit card payments, processing customer data, etc. However, not all of them employ experienced developers with all the necessary skills. Build your digital infrastructure using certified third-party software and help from IT outsourcing providers.
Secure Solutions
Employing software providers and SaaS platforms (for instance, a property management system, PMS) means an extra budget. However, those investments are far smaller than the fines you will pay in case of a data breach. Such providers employ teams of professionals who take security very seriously and will keep hackers at bay.
Minimized Data
Store as little personal data as you can. Collecting large volumes of data, despite its upsides, makes you more vulnerable to cyberattacks.
If you absolutely need to accumulate some data, look for storage services. A secure third-party server requiring multiple checks to access the information may be a great option. Another way is to use software, storing sensitive data on your customers’ devices and accessing it only when required.
Risk Mitigation
Design a plan for how to deal with a data breach. Despite your best efforts, criminals might still attack your business. A fast and efficient response can help mitigate damage to a brand’s finances and reputation.
Things to Consider When Implementing Data Security Solutions
When implementing cyber security for hospitality, there are several important considerations to protect sensitive information and the overall security of your organization’s data.
Scalability
As your hospitality business grows, you will likely collect and process more guest data, including personal and financial information. The same is true for expanding to new locations or markets. Scalability ensures that your data security measures can handle this increased volume without compromising protection.
The hospitality industry often experiences seasonal fluctuations in demand. Scalable solutions can expand capacity during peak seasons when you have more guests and shrink it during slower periods to optimize resource utilization.
Ease of Integration
Ensure your data security solution is compatible with the software and hardware components used in your hospitality operations. This includes property management (PMS), point-of-sale (POS), and guest reservation systems. Choosing security solutions that offer robust Application Programming Interfaces (APIs) is a must.
Data formats and structures can vary between systems. Make sure your security solution can handle data mapping and transformation tasks, converting data from one format to another as needed for integration.
Access Control and Authentication
Role-based access control (RBAC) enhances security by limiting access to only what is necessary for each user’s job function, reducing the risk of unauthorized data exposure. For example, front desk staff might gain entry to contactless check-in/check-out systems, and IT administrators may access system configurations with limited availability in guest rooms.
Multi-factor authentication (MFA) helps protect against unauthorized access, even if login credentials are compromised, as an additional factor is required for authentication. This includes something you know (password or PIN), have (mobile app or hardware token), and are (biometric data like fingerprints, retina scans, or facial recognition).
Single Sign-On (SSO) simplifies user access management by allowing users to log in once and gain access to multiple systems or applications with a single set of credentials, further streamlining security and access control processes.
Many organizations use identity management systems (IDM) to centrally manage user identities, access permissions, and authentication policies. When evaluating a data security solution, ensure it can integrate with your existing IDM system.
Cloud Security
For the cyber security hotel industry, it’s essential to choose verified cloud providers known for their strong security measures and commitment to data protection. For example, Amazon Web Services (AWS), Microsoft Azure, and Google Cloud.
Ensure that sensitive guest information and business data are encrypted both in transit (protocols such as TLS/SSL) and at rest. That means that even if unauthorized individuals gain access to the cloud infrastructure, the data will remain protected and unreadable.
Data Privacy Compliance
Healthcare organizations handle significant amounts of guest data that may include personal and sensitive information.
Ensure compliance with relevant data privacy regulations, such as the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and Health Insurance Portability and Accountability Act (HIPAA). They include the right to know what data is collected and shared, the right to opt out of data sales, and the right to have data deleted.
Boost Your Hotel Cyber Security with Acropolium
Hotels are hubs for the personal data of many people and numerous financial operations, which lures cybercriminals. To boost cyber security in hotel industry, you need to keep software up-to-date, paying special attention to POS’s. Also, you should look for trustworthy bespoke software providers or SaaS platforms for your critical operations.
Acropolium has been working with clients in the hospitality sector for over 12 years. Our team delivered 45 custom solutions and provided consulting services for more than 70 projects. Acropolium’s IT solutions spectrum ranges from POS software to delivery apps. And here are our latest cases:
Hospitality Property Management System
A hospitality company approached us to develop a Property Management System (PMS) to manage service, pricing, reservations, payment collection, and revenue reporting. It was important to synchronize the platform with the Airbnb and Booking.com booking channels, as well as Pipedrive, to handle the sales pipeline and financial reporting.
The solution we created helped us improve the company’s operational efficiency by 37%, reduce administrative costs by 40%, and increase the number of reservations by 30%.
Hotel Chain Management Software
A leading hotel chain in Ukraine wanted to optimize its current hotel management solution. Based on it, we created a new platform supporting multiple tenants, improved information processing speed, and moved everything to the cloud. We have added promotions, special offers, and loyalty programs. The company also received a mobile application for iOS and Android.
As a result, the new platform optimized operational systems by 100%, reduced costs by 40%, and increased annual profit by 30%.
If you need a secure data management solution for a hospitality business, contact our dedicated team.








![Contactless Solutions for Hotels [Check-in software, Booking and more]](/img/articles/contactless-solutions-for-hotels/img01.jpg)
![Travel App Development: Cost & Essential Features [2024 Guide]](/img/articles/travel-application-development/img01.jpg)
![How to Develop a Custom Hotel Reservation Software in [2024]](/img/articles/custom-hotel-booking-system/img01.jpg)

![IoT in Hospitality [5 Ways to Grow Your Hotel Business]](/img/articles/iot-in-hospitality/img01.jpg)