
In healthcare technology, security often starts with a typical statement: “We’re HIPAA compliant.” However, HIPAA compliance is only the legal minimum, not a comprehensive defense. It ensures that Protected Health Information (PHI) is handled according to US law, but it doesn’t define how to manage risk, measure resilience, or govern security across complex digital ecosystems.
Modern healthtech companies operate far beyond the boundaries for which HIPAA was written. Patient data now moves through mobile apps, APIs, AI models, analytics pipelines, and multi-cloud infrastructures, environments where regulatory compliance alone can’t guarantee control.
That’s where ISO 27001 and ISO 27701 come in. These international standards don’t replace HIPAA; they extend it. ISO in healthcare builds an Information Security Management System (ISMS), a living framework that continuously identifies and measures risk across people, processes, and infrastructure.
This guide examines critical gaps in HIPAA compliance vs ISO 27001, and adopting these standards becomes the more intelligent, sustainable choice for healthtech companies ready to grow securely.
Why “we’re HIPAA compliant” is not a strategy
Being HIPAA-compliant means that an organization meets the minimum legal threshold for handling PHI. HIPAA compliance is mandatory but fundamentally reactive: it focuses on documentation, enforcement, and penalties after something goes wrong. In contrast, a mature healthcare cybersecurity strategy anticipates risk, documents accountability, and continuously adapts to technological and regulatory change.
According to McKinsey Risk & Resilience research, the average cost of a successful cyber incident now exceeds $5 million, while organizations still take an average of 73 days to contain a breach. These figures highlight a persistent gap between compliance and control: most healthcare companies can demonstrate adherence to HIPAA on paper, yet struggle to detect and contain threats in real time.
What is the difference between legal compliance vs managed security?
HIPAA compliance is a legal requirement. It defines what must be protected, not how to manage protection across the enterprise. It’s enforced by the US Department of Health and Human Services’ Office for Civil Rights, usually after a breach or complaint.
On the other hand, ISO 27001 is a management standard, a framework for building and maintaining a living security system. It integrates people, processes, and technology into an ISMS, governed by the Plan–Do–Check–Act cycle.
When organizations focus only on HIPAA’s static safeguards, they often end up with disjointed compliance efforts:
policies written for auditors, not for engineers;
risk assessments performed once a year but never revisited;
vendor contracts that reference “best efforts” without verified oversight.
ISO 27001 healthcare replaces that fragmentation with structure: defined ownership, measurable risk treatment, and continuous improvement embedded in day-to-day operations.
What a HIPAA-only approach often misses
HIPAA’s scope is deliberately narrow: to protect PHI. It does not prescribe managing other sensitive data, governing suppliers, or sustaining ongoing security maturity. As a result, many “HIPAA-compliant” organizations face recurring weaknesses in four key areas:
1. Vendor risk management
HIPAA addresses third-party risk primarily through Business Associate Agreements (BAAs). These contracts confirm legal accountability. A covered entity may meet its HIPAA obligations while lacking visibility into how its cloud vendors, healthcare software development providers, or offshore developers secure PHI. ISO 27001 for healthcare closes this gap through documented third-party risk management, supplier due diligence, and control verification.
2. DevSecOps integration
HIPAA’s Security Rule is intentionally technology-neutral, which leaves implementation details to each organization. The risk is that security becomes an afterthought in the software lifecycle. ISO 27001 mandates secure system acquisition, development, and maintenance as a continuous process. Security testing, code review, and access management are integrated from the design phase onward.
3. Continuous monitoring and evaluation
HIPAA requires periodic assessment but does not specify cadence, metrics, or scope. ISO in healthcare formalizes monitoring and review, requiring organizations to track control effectiveness, and incident responses within defined intervals. The outlined structure creates a feedback loop where lessons from incidents directly inform new controls.
4. Data lifecycle and scope
HIPAA protects PHI and only PHI. It does not extend to other forms of sensitive information, which are often equally critical to healthcare operations. ISO 27001 for healthcare covers all information assets, regardless of their type or source. ISO 27701 extends this by embedding privacy management into the ISMS, addressing the full lifecycle of Personally Identifiable Information (PII) from collection to deletion.
These limitations are becoming more visible as healthcare expands beyond traditional settings. IEEE reports that emerging tele-ICUs and hospital-at-home programs now depend on fully connected systems that require stronger end-to-end security and interoperability. 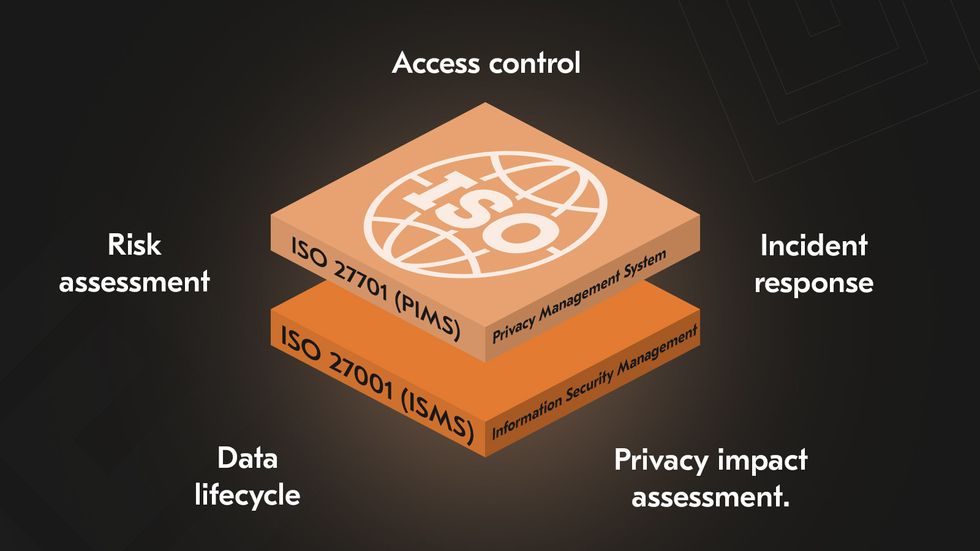
What ISO 27001 delivers in practice
ISO 27001 defines a continuous management system for information security, known as the ISMS. It is the organization’s foundation for identifying risks, implementing controls, and improving performance over time.
Context and scope
Every implementation begins with establishing context: what information needs protection, where it resides, and which risks are material. The scoping step includes identifying internal and external factors that influence security performance. Unlike HIPAA, ISO 27001 protects all critical data assets and provide organizations complete visibility over their security landscape.
Risk management and control selection
ISO 27001 is built on risk-based thinking. Each organization must conduct a structured assessment to identify threats, evaluate their likelihood and impact, and prioritize mitigation. Controls are selected from Annex A (a catalog of 93 measures covering governance, access, encryption, incident response, and supplier security). The process is documented through the Statement of Applicability, a key artifact that outlines which controls are implemented and why.
Continuous improvement
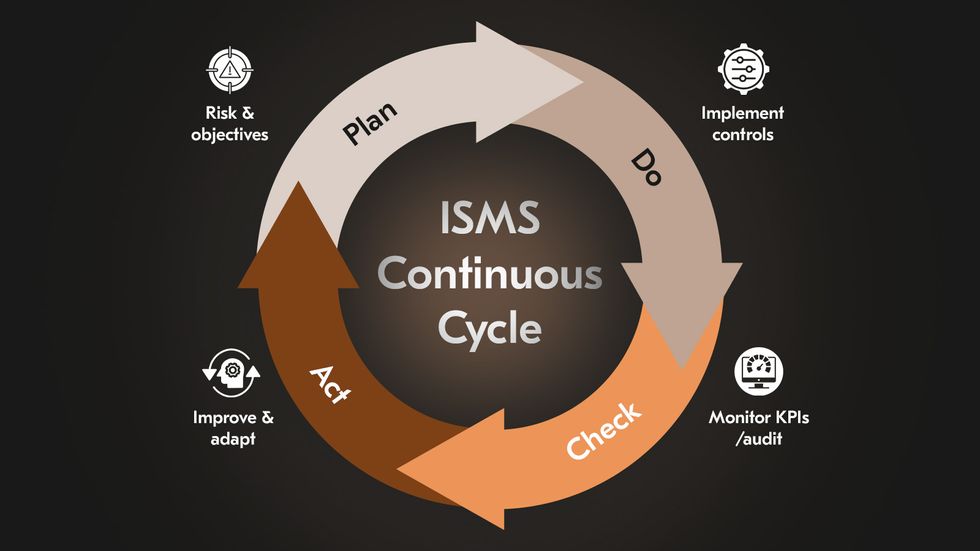
At the core of the ISMS is the Plan–Do–Check–Act cycle, the engine that drives continuous improvement. This cycle ensures the ISMS evolves alongside the organization’s growth and threat landscape.
Plan: Define objectives, risks, and controls.
Do: Implement policies and security measures.
Check: Monitor performance through KPIs, audits, and incident reviews.
Act: Refine and improve based on lessons learned and changing risks.
How ISO 27001 accelerates enterprise sales and partnerships
Beyond compliance, ISO 27001 creates tangible commercial value. In healthtech markets where due diligence can slow contracts by weeks, certification assures potential partners, investors, and clients that security is systematically managed and externally validated.
Building trust and competitive advantage
ISO 27001 certification signals that your controls meet international best practices and are regularly audited. It also reinforces credibility with regulators, accelerating the onboarding of new products and partners.
Streamlining vendor due diligence
Certification minimizes the administrative weight of vendor assessments. Enterprise buyers frequently require ISO 27001 certification as proof of due diligence, eliminating the need for repetitive security questionnaires. The standard’s built-in supplier management controls (Annex A.15) also ensure your vendor ecosystem meets the same level of assurance. For growing healthtech firms, this alignment between internal security and client requirements cuts response cycles dramatically and builds trust into the procurement process.
Operational efficiency and cost reduction
The ISMS encourages consistency and reusability: “implement once, comply many.” Controls designed under ISO 27001 can be mapped directly to other frameworks like GDPR and SOC 2, allowing teams to manage overlapping requirements through a unified system. Over time, organizations see fewer incidents, lower remediation costs, and shorter audit cycles.
ISO 27701: When privacy becomes a product advantage
Privacy in healthcare is a defining measure of product credibility. ISO/IEC 27701, the Privacy Information Management System (PIMS) standard, extends ISO 27001 beyond security to establish a structured model for privacy governance. For healthtech companies, adopting it signals more than compliance; it reflects maturity in how the organization handles, safeguards, and demonstrates control over personal data.
While HIPAA sets the legal foundation for PHI in the US, its scope ends where broader data accountability begins. ISO 27701 closes that gap. It introduces globally recognized mechanisms for managing privacy risks, mapping responsibilities across the supply chain, and proving due diligence.
How to map PII controller and processor roles in healthtech business models
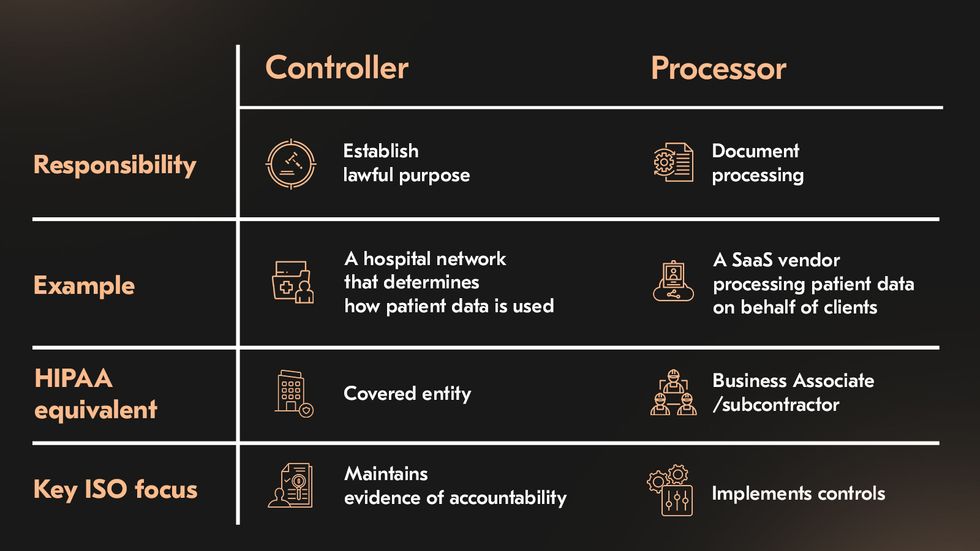 Healthtech ecosystems are rarely linear. A telemedicine platform may collect patient data through an app, store it in the cloud, and integrate with diagnostic systems or insurance APIs. ISO 27701 helps define accountability across this network by introducing two fundamental roles:
Healthtech ecosystems are rarely linear. A telemedicine platform may collect patient data through an app, store it in the cloud, and integrate with diagnostic systems or insurance APIs. ISO 27701 helps define accountability across this network by introducing two fundamental roles:
| Role | Healthtech business example | Corresponding HIPAA role | ISO 27701 focus |
|---|---|---|---|
| PII Controller | A hospital network that determines how patient data is collected and used | Covered entity | Establishes lawful purpose, processing boundaries, and retention periods; maintains evidence of accountability. |
| PII Processor | A SaaS telemedicine vendor processing patient data on behalf of healthcare clients | Business Associate/ subcontractor | Implements operational, technical, and organizational controls; documents data flows and risk treatment actions. |
This distinction clarifies responsibilities that HIPAA leaves implicit. Under ISO 27701, controllers and processors must document processing activities, assess privacy risks, and ensure that contractual obligations are supported by evidence of control.
How ISO 27701 closes HIPAA privacy gaps
HIPAA defines what must be protected; ISO 27701 specifies how privacy protection operates as a continuous, auditable process. It bridges the space between compliance and governance and helps answer the practical questions HIPAA often leaves open.
What happens when your data extends beyond PHI? HIPAA applies strictly to PHI, while ISO 27701 covers all forms of PII, from staff and research data to financial or device-generated information, which still carries privacy risks.
Who is accountable for privacy decisions and documentation? ISO 27701 formalizes privacy governance, embedding responsibility within the medical management system. It requires documented processing activities, privacy impact assessments, and clear accountability records.
How can privacy risks be treated systematically across the organization? HIPAA’s Security Rule focuses narrowly on ePHI. ISO 27701 enforces a unified, risk-based approach across all information assets and integrates privacy into enterprise-wide risk management.
How do you prove that privacy controls actually work? Certification under ISO 27701 requires tangible, verifiable evidence, confirming that privacy controls are active, effective, and continuously improved.
What if your operations cross borders or handle global data flows? ISO 27701 aligns privacy governance with frameworks such as GDPR, CCPA, and other national regulations, allowing one integrated system to address multiple legal regimes while maintaining consistent assurance.
Put simply, HIPAA keeps healthcare organizations compliant; ISO 27701 makes them accountable. Together, they create a privacy architecture that’s a lawful and scalable foundation where compliance supports growth.
HIPAA vs ISO 27001/27701: What to choose and when
The choice between relying solely on HIPAA compliance or expanding to ISO 27001 and 27701 certification depends on how far your organization needs to go beyond minimum regulatory requirements.
HIPAA ensures lawful handling of PHI in the US, but it stops short of defining how to manage information security across systems, vendors, and international operations.
ISO 27001 and 27701 establish a structured, auditable management system for security and privacy that scales globally, integrates into business processes, and provides verifiable proof of due diligence.
Let’s discover the difference between HIPAA vs ISO 27001 below.
| Aspect | HIPAA | ISO 27001/27701 |
|---|---|---|
| Scope | US federal regulation governing how healthcare entities protect ePHI under the Privacy and Security Rules. | International standards defining a complete ISMS/PIMS that covers all information assets |
| Scalability | Flexible but limited to healthcare and related vendors. | Framework designed for continuous improvement and adaptable to any size, sector, or technology stack. |
| International reach | Applicable only within the United States. | Recognized worldwide; certification demonstrates compliance with global best practices |
| Vendor risk | Relies on BAAs to extend liability to third parties handling PHI | Requires a documented third-party risk management process |
| Evidence depth | Focuses on documenting safeguards and risk analyses specific to PHI | Requires comprehensive documentation across the ISMS / PIMS |
| Audibility | Compliance verified through investigations or audits by the HHS Office for Civil Rights | Formal certification issued by accredited auditors |
| Cost of ownership | Lower upfront cost but high exposure to non-compliance penalties | Higher initial investment but reduced long-term compliance cost |
| Impact on go-to-market | Mandatory entry requirement for operating in the US healthcare ecosystem. | Provides verifiable assurance to enterprise partners and global clients |
How to choose between HIPAA vs ISO

HIPAA vs ISO 27001 are not competing but complementary. When HIPAA defines the legal floor for handling PHI within the United States, ISO 27001/27701 establishes a repeatable operating model that scales across geographies, business units, and data types.
When ISO in healthcare is integral for:
The organization that manages data across countries or collaborates with healthcare providers and technology partners.
Clients or enterprise buyers who request third-party validation of security posture.
Information extends beyond PHI, requiring unified protection measures.
Management seeks structured risk management, regular internal audits, and measurable KPIs for cyber resilience.
The organization that handles personal data under additional privacy regimes, where ISO provides alignment and proof of compliance.
Certification differentiates the company, shortens presales due diligence, and improves partner onboarding.
When HIPAA plus strong internal processes are sufficient:
Operations are wholly domestic, with all data confined to the US healthcare context.
The business handles only PHI, and information assets outside this scope pose minimal risk.
The objective is to meet statutory requirements without pursuing external certification or global scaling.
Budget or personnel capacity limits the ability to establish a full ISO-compliant ISMS.
In practice, the most efficient strategy is to use HIPAA as a mandatory baseline and build ISO 27001/27701 on top. HIPAA compliance vs ISO 27001 integration allows organizations to unify policies, automate evidence collection, and reuse controls across multiple regulatory frameworks.
Success story of strengthening security maturity in a telemedicine SaaS platform
A veterinary telemedicine provider approached Acropolium after reaching a critical growth point.
Initial challenge
The platform already complied with HIPAA-equivalent safeguards for handling health data and online consultations, yet compliance alone was no longer sufficient. As the company expanded partnerships with hospitals, insurance systems, and pharmacy networks, clients requested structured evidence of security governance, vendor oversight, and privacy-by-design practices.
Our solution
Acropolium led the company through a nine-month roadmap to strengthen its compliance model and prepare for ISO 27001 and 27701 certification. The initial gap assessment revealed fragmented documentation and 37 unverified controls across cloud infrastructure, access management, and third-party integrations. Within the first quarter, we implemented a unified risk register, automated access reviews, and incident response protocols mapped to ISO 27001 Annex A.
In the second phase, privacy management under ISO 27701 was embedded into day-to-day operations. We introduced data classification and consent policies, clarified veterinary clinic data controller/processor roles, and formalized medical imagery and chat records retention rules.
The outcomes
By certification, the impact was tangible. The company reduced presales security review time, standardized vendor assessments, and improved transparency for partners handling prescription data. ISO 27001/27701 certification proved that the platform managed security and privacy as an integrated, measurable system. 
How we guide your security and compliance journey
Proper compliance is a system that evolves with every product release and every new data flow. Acropolium helps organizations move from isolated compliance efforts to a sustainable, measurable security and privacy management model within HIPAA compliance vs ISO 27001.
From roadmap to certification: our approach
Achieving ISO 27001 or 27701 certification involves constructing a system that continuously measures, improves, and demonstrates how your organization manages risk and privacy. Acropolium guides healthtech companies through a structured, evidence-based roadmap that balances regulatory compliance with practical engineering.
The process begins with a gap assessment, identifying how current security and privacy practices align with ISO 27001 and HIPAA requirements.
Next comes the risk model and assessment. Here, we analyze potential data confidentiality, integrity, and availability threats.
The third step involves policies and controls. We work with clients to develop or refine security and privacy policies that govern every part of data handling, from access control and encryption to incident response and vendor oversight.
Once the policies are in place, we support internal audits. These audits are essential for verifying whether controls are HIPAA compliance vs ISO 27001 implemented and effective. Internal reviews uncover operational gaps early and prepare organizations for the rigor of external certification.
Finally, we assist in preparing for external audits. Acropolium helps teams gather and organize the evidence auditors expect, and ensures the ISMS or PIMS functions as intended. After certification, we provide ongoing support through surveillance audit preparation, evidence updates, and policy revisions, maintaining compliance.
How we integrate HIPAA vs ISO 27001 into the software development lifecycle
Our process begins with threat modeling, which is performed early in product design. This step identifies potential attack vectors and data exposure points across architecture layers. We then implement Infrastructure-as-Code controls, embedding security policies into automated deployment scripts and CI/CD pipelines. We help clients configure centralized logging pipelines that capture relevant events across medical applications, infrastructure, and APIs.
The final piece is evidence management. Both HIPAA and ISO frameworks depend on documentation that proves ongoing control effectiveness. We design documentation and evidence collection processes that are lightweight but audit-ready, covering policies, risk assessments, test results, and operational metrics.
Need a starting point? Get our free ISMS and PIMS policy templates, practical examples to help you structure your documentation, assign responsibilities, and align with ISO control requirements before you begin the certification process.
Final thoughts
HIPAA compliance may open the door to healthcare markets but it doesn’t keep it locked. As digital health platforms scale, data flows between cloud environments, third-party APIs, and analytics pipelines, areas HIPAA was never designed to govern. ISO 27001 and ISO 27701 fill the gap by embedding risk and privacy management into everyday operations.
We’ve seen how structured security maturity drives real business growth. Three of our clients started as early-stage startups and grew into unicorns. Four are part of the Fortune 500. Several have trusted us with partnerships spanning more than ten years. We’ve delivered over 450 applications and guided 148 organizations toward resilient, compliant, and enterprise-ready systems.
If your healthtech product is ready for that next level of assurance, book a free ISO 27001/27701 gap assessment with Acropolium. We’ll help you understand your current posture, identify fundamental gaps, and build a sustainable HIPAA compliance vs ISO 27001 security model that grows with your business.







![AI in Healthcare: Examples, Use Cases & Benefits [2025 Guide]](/img/articles/ai-in-healthcare-examples-use-cases-and-benefits/img01.jpg)
![Online Pharmacy App Development [2025 Guide]](/img/articles/pharmacy-app-development/img01.jpg)
![Machine Learning in Healthcare: [9 Real Use Cases Included]](/img/articles/machine-learning-in-healthcare-use-cases-benefits-and-success-stories/img01.jpg)

![EMR/EHR Software Development: [Benefits & Best Practices]](/img/articles/emr-ehr-software-development-implementation-tips-and-cost/img01.jpg)